Whenever you send private data to another computer or server on the Internet, which you do many times a day,Once you send the data packets of your voice call, chat, email or credit card number over the jungle of the Internet, you have no control over who lays their hands on them. This is the nature of the Internet.This is what makes so many things running on it free, including Voice over IP, which gives you free calls. Your data and voice packets pass through many unknown servers, routers, and devices where any hacker, big brother or rogue state agent can intercept them.
Today, end-to-end encryption is part of your daily digital life. It is actually the ultimate security mechanism that protects your sensitive and private data online, like your credit card number during a transaction, or your phone call which is being wiretapped.
The very first instant messaging and calling apps that came with end-to-end encryption like internet calling, VoIP and instant messaging apps like WhatsApp, Facebook Messenger.
End-to-End Encryption (E2EE) :
- End-to-end encryption (E2EE) is a method of secure communication that prevents third-parties from accessing data while it's transferred from one end system or device to another.
- In E2EE, the data is encrypted on the sender's system or device and only the recipient is able to decrypt it.
- End-to-end encryption is an implementation of asymmetric encryption.
- As the name implies, end-to-end encryption protects data such that it can only be read on the two ends, by the sender, and by the recipient. No one else can read the encrypted data, including hackers, governments, Internet service provider, application service provider or tamper with it.and even the server through which the data is passing.
WhatsApp Example :
- Consider two WhatsApp users (Bob and Alice ) communicating through instant messaging or calling over the Internet. Their data passes through a WhatsApp Server while transiting from Bob to Alice.
- First Bob sends a message to Server and this message is saved at the Server and then sent to Alice. The main draw back of this method is that, if a 3rd person or hacker who is interested in this message being sent from Bob to Alice tap in the communication line between Bob and Server and gets to know all the messages that is being sent from Bob to Server.
- To avoid this, a most secure form of communication was introduced, where Bob first encrypts the message and then sent it to the Server. In this way if the hacker tries to hack the communication line between Bob and Server won't get to know the message that is being sent from Bob to Server and the message once its arrived at Server is decrypted and saves at Server and the message is again encrypted and sent to Alice.
- In this way the message is transferred from Bob to Alice , but the main drawback of this method is if a person who is working at the Server gets to know the message being sent from Bob to Alice as the message is decrypted and saved at Server .Since the hacker can't tap the communication line between Bob and Server , know he can directly hack the Server and get to know the communication happening between Bob and Alice.
- To avoid the drawback end to end encryption was introduced where the message is first encrypted by Bob and then send to Server, but here the message is not decrypted and saved at Server. Instead this message is forwarded directly to Alice, with this message the main advantage is the hacker if he hack the communication line between Bob and Server , he won't get to know what message is being sent from Bob to Server and Also if he wants to hack the Server then he won't get to know what message is being sent from Bob to Alice. because the messages are not saved at Server and the person who is working on the Server won't get to know the what message is being sent since the messages are not decrypted and saved at Server.
End-to-end encryption (E2EE) in the payments processing chain (payments industry)
- As E2EE is the generic terminology used by the IT industry to describe any solution that encrypts communications from one endpoint to another endpoint. Some businesses also use end-to-end encryption (E2EE) to protect credit card information. Examples of E2EE include IPSec, SSL and TLS.
- In E2EE key management of the encryption can be done by any party that has an endpoint such as a merchant or a service provider.
Drawbacks of E2EE
- While third party key management is typically acceptable for small merchants, this does not work for merchants that switch their own transactions to various processors as do mid-sized and large merchants.
Point-to-Point Encryption (P2PE) :
- P2PE is a subset of E2EE .With P2PE, your customers’ credit card information is automatically encrypted whenever they swipe their plastic at the counter. That information remains encrypted when sent directly to your payment processor.Although this credit card data still travels over unsecured Wi-Fi and cellular networks, unauthorized parties are unable to decode the information. Only the payment processor has the encryption key on its end.
- Point-to-point encryption (P2PE) is a standard established by the PCI Security Standards Council. Payment solutions that offer similar encryption but do not meet the P2Pe standard are referred to as end-to-end encryption (E2Ee) solutions.
- It has been validated by a third party Quality Security Assessor and have been certified to the PCI P2PE standard.
- Under the P2PE standard, only the transaction processor or other third party is allowed to perform key management. The merchant is never allowed to perform encryption key management under the P2PE standard. As a result, DUKPT can be used by both P2PE and E2EE solutions.
- Point to Point Encryption (P2PE) ensures that credit card data that must be collected and transmitted after a purchase is encrypted by a one time encryption key as soon as the card is swiped into the card reader. That key is destroyed immediately after a single use.
A True P2PE solution is determined with three main factors:
- The solution uses a hardware-to-hardware encryption and decryption process along with a POI device that has SRED (Secure Reading and Exchange of Data) listed as a function.
- The solution has been validated to the PCI P2Pe Standard which includes specific POI device requirements such as strict controls regarding shipping, receiving, tamper-evident packaging and installation.
- A solution includes merchant education in the form of a P2PE Instruction Manual, which guides the merchant on POI device use, storage, return for repairs and regular PCI reporting.
P2PE Decryption Key Storage :
- Key storage and decryption happens in an isolated Hardware Security Module (or HSM) that have been validated by PCI and/or FIPS 140-2 level at the payment gateway. SafeNet's HSMs are at the foundation of the only Point to Point Encryption solutions to be validated to date.
- P2PE is a special case where encryption is applied within a retail point-of-sale (POS) terminal.If the P2PE process is implemented correctly, with account data being encrypted within an approved, secure cryptographic device (SCD), such as a POS terminal, and not decrypted at all within the merchant environment, there is potential for the merchant to be taken almost completely out of scope for PCI DSS.
- For P2PE to work as intended, strict controls for protection of and access to decryption keys must be in place. The current guidance requires the use of hardware security modules (HSMs) with an appropriate security rating to protect access to those keys.From a PCI DSS perspective, any system that has the capacity to decrypt account data comes into scope immediately, so the ability to insulate merchants by protecting keys within HSMs can have significant benefits for all concerned.
Hardware-Based Encryption Devices (HSM and TPM):
TPM and HSM are two types of hardware modules used for encryption. Trusted Platform Module (TPM) and a hardware security module (HSM) can be used for hardware encryption.
HSM :
- A hardware security module (HSM) is a security device you can add to a system to manage, generate, and securely store cryptographic keys.
- High performance HSMs are external devices connected to a network using TCP/IP. Smaller HSMs come as expansion cards you install within a server, or as devices you plug into computer ports.
- One of the noteworthy differences between the two is that HSMs are removable or external devices. In comparison, a TPM is a chip embedded into the motherboard. You can easily add an HSM to a system or a network, but if a system didn’t ship with a TPM, it’s not feasible to add one later. Both provide secure encryption capabilities by storing and using RSA keys.
- Vendors : Thales, Gemalto, Utimaco, Ultra Electronics - CIS, Atalla, Futurex, and IBM.
TPM :
- A Trusted Platform Module (TPM) is a hardware chip on the computer’s motherboard that stores cryptographic keys used for encryption. Many laptop computers include a TPM, but if the system doesn’t include it, it is not feasible to add one. Once enabled, the Trusted Platform Module provides full disk encryption capabilities. It becomes the "root of trust" for the system to provide integrity and authentication to the boot process. It keeps hard drives locked/sealed until the system completes a system verification, or authentication check.
- The TPM includes a unique RSA key burned into it, which is used for asymmetric encryption. Additionally, it can generate, store, and protect other keys used in the encryption and decryption process.
- Vendors : Microsoft,Infineon,Google,Atmel,Oracle ships ,PrivateCore vCage,VMware ESXi ,Taiwanese ,Xen ,KVM
Drawbacks of P2PE
- The huge downside to P2PE for merchants is that once you decide on a given P2PE solution, you are pretty much stuck with it and the processor providing it. That is because most processors offering P2PE are only offering one P2PE solution. As a result, if a better deal comes along for processing your transactions, you will likely have to replace your terminals and possibly other equipment to switch to the new processor. For some merchants, that could be a costly proposition and make any switch not worth the effort.
Objective of E2EE and P2PE
- When you relay credit card data to your payment processor through a terminal,that information is usually sent over an unsecured network. With the right tools, anyone can theoretically intercept this information and begin racking up fraudulent charges.
- E2EE is a generic term that describes any solution that encrypts communications from one endpoint to another endpoint. This makes P2PE a subcategory of E2EE. Both are methods of encryption that process payment card data when transactions are made at a POS (point-of-sale) terminal, or POI (point of interaction).
- End-to-End Encryption (E2EE) and Point-To-Point Encryption (P2PE), are the two main ways that payment card data is protected when a transaction is made at a Point-of-Sale (POS) terminal.
- The objective of P2Pe and E2Ee is to provide a payment security solution that instantaneously converts confidential payment card (credit and debit card) data and information into indecipherable code at the time the card is swiped to prevent hacking and fraud. It is designed to maximize the security of payment card transactions in an increasingly complex regulatory environment.
Difference between E2EE and P2PE
- E2E systems are not validated by the PCI Council. They’re offered by banks or other third parties as a way to securely transmit card data.
- In E2EE key management of the encryption can be done by any party that has an endpoint such as a merchant or a service provider. However, under P2PE, the key management must be done by a processor or other third party, not the merchant.
- With P2PE, the transmission link between merchants and payment processors is direct. By contrast, E2EE often relies on indirect relays, which create more opportunities for data interception.
- Anyone can technically set up an E2EE connection and manage the encryption keys in house, but only payment processors are authorized to maintain these keys when using P2PE
- While the two technologies are similar i,e both encryption technologies are secure, P2P provides an element of security and certainty that E2E is unable to match at this point. Hence P2PE offers much greater protection.
P2PE Solution Provider
- The P2PE solution provider is a third-party entity (for example, a processor, acquirer, or payment gateway) that has overall responsibility for the design and implementation of a specific P2PE solution, and manages P2PE solutions for its merchant customers. The solution provider has overall responsibility for ensuring that all P2PE requirements are met, including any P2PE requirements performed by third-party organizations on behalf of the solution provider
- Both P2PE and E2EE solutions encrypt payment data at point-of-interaction with the payment type (Swipe/MSR, Dip/EMV, Tap/NFC). From there, the data will be transported to the solution provider which, depending on the type of solution, will occur in a non-integrated, semi-integrated or fully-integrated fashion.
- The solution provider, which is almost always a payment gateway or back-end processor, will decrypt the data for processing. For payment gateways, the packet is decrypted, and then sent to the relevant processor for processing in an encrypted, clear-text fashion.
- That being said, the connection to back-end processor, such as First Data or Elavon,is usually over a direct circuit or through a SSL/TLS-encrypted tunnel.
PCI P2PE Requirements
- Secure encryption of payment card data at the point of interaction (POI)
- P2PE validated application(s) at the point of interaction
- Secure management of encryption and decryption devices
- Management of the decryption environment and all decrypted account data
- Use of secure encryption methodologies and cryptographic key operations, including key generation, distribution, loading/injection, administration and usage
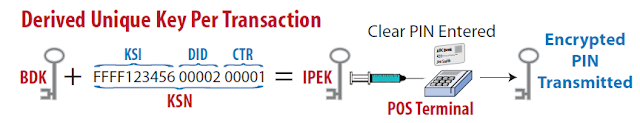
DUKPT (Derived Unique Key Per Transaction):
- One of the most common E2EE solutions used by merchants is derived unique key per transaction (DUKPT) also known as “duck putt”. DUKPT is commonly used in the convenience store and gas station industries to encrypt sensitive authentication data (SAD) from the gas pump to the merchant or processor.
- DUKPT uses the 56-bit data encryption standard (DES) encryption or triple DES (3DES) algorithms. While DES and 3DES 56-bit and 112-bit are no longer considered secure, because DUKPT uses a unique key for every transaction, it means that every transaction has to be individually broken to gain access to the data.
For more details about DUKPT , click on this link https://www.java2depth.com/2019/03/dukpt-in-java-using-jpos.html?spref=fb&m=1
Inform:







The average response time for a user to reply to a text message is 90 seconds. Did you know this? You can also know about other facts related to this topic including how to text from a landline service. Visit the website to know more.
ReplyDeleteVery informative blog.Much thanks again. Much obliged. thermal oxidizer
ReplyDeleteThis becomes a threshold issue in non-cash payments, which often involve technical issues such as the establishment of a means of communicating over distance, ability to verify the parties in a payment transaction, and many other factors.소액결제현금화
ReplyDeleteThe manner in which you profit in business is to continue rehashing a similar procedure again and again as per the framework you have created. This is particularly the way. 소액결제현금화
ReplyDeleteI am definitely enjoying your website. You definitely have some great insight and great stories. 소액결제현금화
ReplyDeleteThe article was up to the point and described the information very effectively. Thanks to blog author for wonderful and informative post.
ReplyDeleteSecurity Solution consultant
As of late, Nigerians took an interest in the in-nation manufacture of six modules of the Total Egina Floating Production Storage Offloading (PSO) vessel and coordination of the modules on the FPSO at the SHI-MCI yard. certificazione ISO 9001 DNV
ReplyDeleteYour work is truly appreciated round the clock and the globe. It is incredibly a comprehensive and helpful blog. 신용카드 현금화
ReplyDeleteGood one! Thanks for sharing informative blog like this. Keep blogging
ReplyDeleteRegards,best online payment gateway
Digital Payment Platform
I haven’t any word to appreciate this post.....Really i am impressed from this post....the person who create this post it was a great human..thanks for shared this with us. 소액결제 현금화
ReplyDeleteSuper-Duper site! I am Loving it!! Will come back again, Im taking your feed also, Thanks. 소액결제 현금화
ReplyDeleteImpressive blog you have shared information about payment method. as we also provide Random name generator at affordable price for more info visit our website.
ReplyDeleteI wanted to thank you for this excellent read. Thank you for taking time to know more about in this subject. as we provide cloud phone system at affordable prices. for more info visit our website.
ReplyDeleteI would like to say that this blog really convinced me to do it! Thanks, very good post. 소액결제 현금화
ReplyDelete